Recently, we had a client who had an issue trying to enroll himself through an Apple DEP protected Intune based enrollment platform.
Strangely, the guy was able to enroll everything fine into Intune where the device was not connected via DEP. He only ran into problems when the phone was going via the Apple DEP route (where the phone is locked to the organisation – Remote Management).
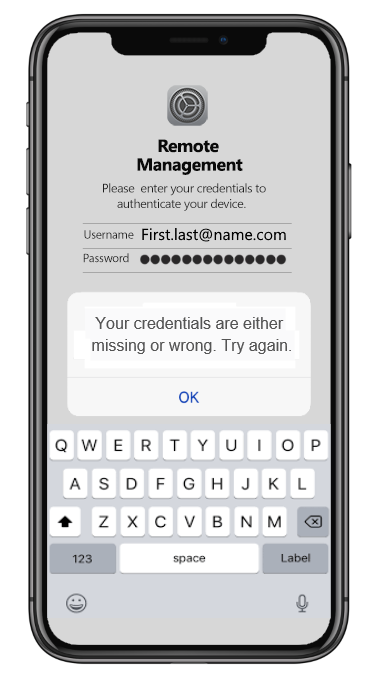
Whilst attempting to sign in, he would see something like the screenshot above where IOS reports a screen with Remote Management – Log in to “Company Name PTY Ltd” with a login prompt.
Each time he would log in the system would report back the following error:
“Your credentials are either missing or wrong. Try again.”
We tried other team members nearby, all logged in successfully. Again, he was able to sign in on devices that were not protected by DEP.
Multi-factor Authentication Status: Forced
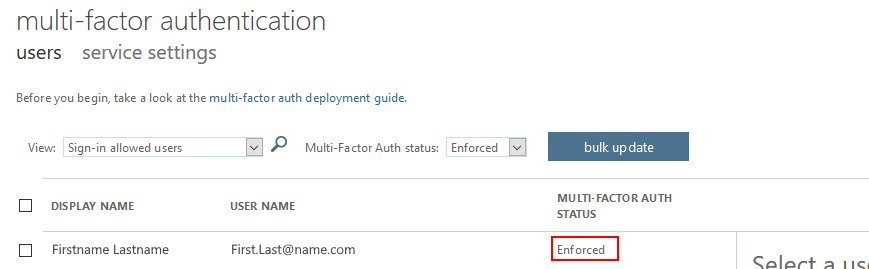
In this case, it turned out that this team member had MFA set to “forced” at the back end within Azure. This method of MFA differs from the standard conditional access you see enabled these days. This was the original MFA interface – often people forget this interface is even there.
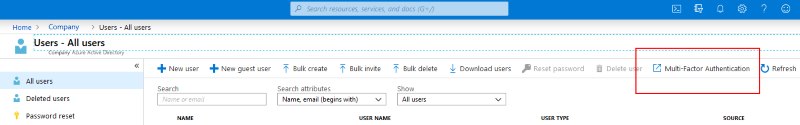
To access this interface, simply log in with an account that has enough access (probably GA is required) either via PIM or otherwise and navigate to the Azure Active Directory Blade and head towards the User – All users section. You will note (if you have enough access) an option across the top of the user tool bar “Multi-Factor Authentication”
Click on the “Multi-Factor Authentication” option. Within the multi-factor authentication screen, search for the affected user and note if “MULTI-FACTOR AUTH STATUS” shows “Enforced”. If it does, either set it to disabled.
Most people are using conditional access these days. Obviously, if you are using this method as your main method of MFA and require it set to forced, you indeed have a problem.
Consider this as a “chicken and the egg” scenario:
Imagine a newly delivered device that has no configuration enabled. How is the end user supposed to be using MFA if their device is fresh out of the box? Generally speaking, most NORMAL end users have only a single device to play with, so having MFA required for a brand new user presents a problem – how can they approve MFA before setting it up?
I am not sure what needs to happen here – do Apple need to change some things to allow for MFA via DEP? does Microsoft need to make an allowance for the initial DEP Call from the Apple DEP servers?
As a work around – it turns out that you can exempt this initial call from MFA within conditional access blade in Azure.
Best of luck out there with “Your credentials are either missing or wrong. Try again.” – Check if MFA is forced in Azure.